Share

In my earlier post I was going on and on about the issues with passwords and how we make the job for the attackers easier. I also mentioned that there are protection mechanisms and small changes in our habits that may help. Now it’s time to go a little bit into detail and see how exactly your credentials can be compromised. Don’t worry I won’t be too technical. I hope 😉
How do they get your password
There are number of techniques used to gain access to a system or an app that’s protected with user credentials. From a quick looksee under the keyboard where you have this very secret post-it note, to elaborate socio-technical scheme aimed in you giving up the access willingly… There are no rules or boundaries. And I mean that. You don’t believe me? Take a look here at what’s possible https://twtext.com/article/1103339953445064704. The original post was removed but if you can carry a big server out from the Datacentre and not be stopped… what can’t you do?
But enough of this fearmongering, just remember, a little bit of paranoia in IT is a good thing. Let me elaborate on some of the most common password attacks, which are:
- Credential stuffing
- Phishing
- Keystroke logging
- Local discovery
- Extortion
- Password spray
- Brute force
- Socio-technical attack
Let’s take a closer look at some of them and analyse them a bit further, trying to answer questions on how easy it is to perform the attack to gain access to a protected system, how effective the attack is and how to protect yourself against the attack.
Credential stuffing
Credential stuffing is just a fancy name for a fairly easy operation. Basically, what you need is data from a recent breach and try reusing that. How to do it? Fairly easy. Just go online and buy stolen credentials from a breach on the Dark Web. It sounds complicated, but with a little will and curiosity you can find such offers in 30 minutes or so.
Offers, like this one, from Polish Dark Web forum Cebulka, can be found without much effort and close-to-none technical skill:
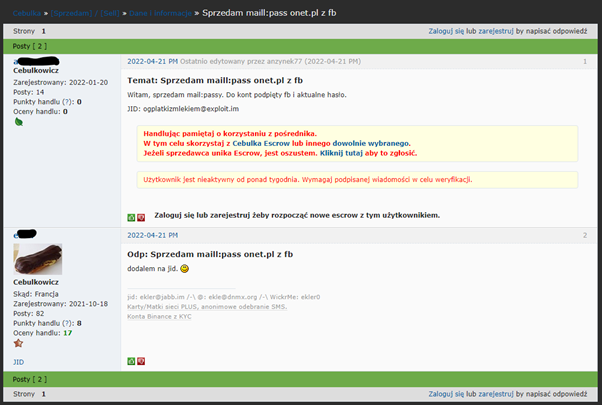
Source: Cebulka – Polish TOR forum
What happens once you got the creds? You take available credentials, test against most popular sites and see where it will take you.
Or hire someone for a relatively small fee for that matter to do it for you:
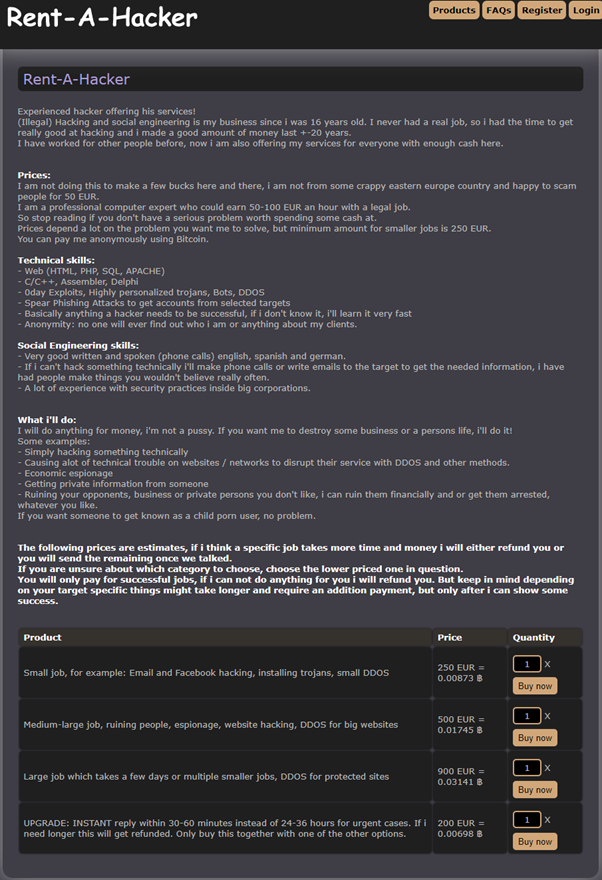
Source: rent-a-hacker dark net site
So…
Is it difficult? No – you can buy credentials online and there are already-made, ready-to-use tools once you have them.
Is it effective? Yes – more than a half of users reuse passwords! This is one of the problems I was going on and on before. Here’s one of the reasons why. You can also bet that millions of attempts are made daily worldwide. You are bound to be tested – be prepared.
How to protect yourself and your users? Once your credentials leak you are open to exploitation. Stop reusing passwords, start to monitor breaches, use password manager and TURN ON MULTI-FACTOR AUTHENTICATION (MFA).
Phishig
This is something you’ve seen for sure. You’re chilling, enjoying your coffee and there it is – an email claiming that someone has shared something with you and a link. You follow the link and see a login page. You’re curious and want to see what was shared, so you logged in, but it doesn’t really look like there’s anything shared there. Well, my friend, you were just phished.
So, how they did it? There are number of tools, free or otherwise, ready to be used to generate counterfeit websites designed to get your username and password. With a good tutorial, you can do it in 30 minutes, no problem, minimal to no skills needed. You don’t even have to understand what’s going on to get those creds if you follow some of the guides to the letter🤯
Is it difficult? Not at all. And this time unique password will not protect you. If you put your credentials there, attackers will know what was simulated and where they can get access.
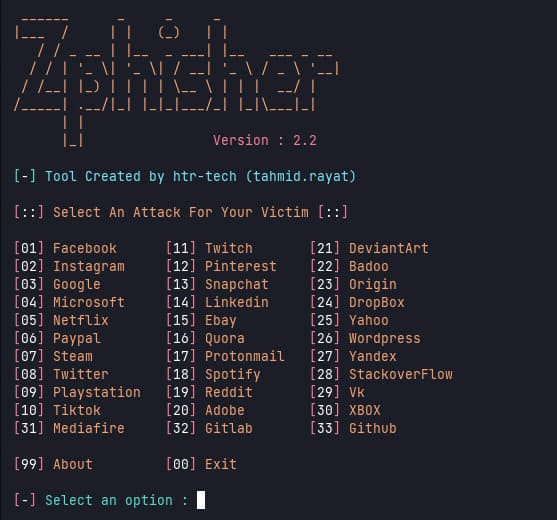
Source: Zphisher tool
Is it effective? Not so much as it could, more than it should. There’s a lot of those emails and this is simply a numbers game. If 0.5% of all inbound emails are phishing scams, you should be more than sure that one day someone in your Organization will get caught.
How to protect yourself and your users? Well… you did give away your username and password. Game over… Or.. did you remember to TURN ON MFA? Change your password either way and monitor services where it might have been used previously, as some passwords reset procedures allow you to change your pass if you know one from the past.
Keystroke logging
To be honest this was a first tool I’ve used. And a long time ago. First time playing with security and knowing little to nothing. I didn’t even know I was a 12-year-old script kiddie. Good thing I was only playing around with some friends from school and our own stuff. Worst that I also got my PC infected. Live and learn I guess 😉
How does it work? Essentially the attackers send you malware that you interact with or save, and you’re hooked. Now they see what you type and where you go on the internet. Fun stuff, huh?
If you think you are protected with an antivirus software or some impenetrable firewalls remember, there are always flaws. Just last week there was a new 0-day vulnerability for Microsoft Word (New Microsoft Office zero-day used in attacks to execute PowerShell (bleepingcomputer.com)). 0-day means that this was not known to the public before and could have been used for some time by attackers to get you infected. This also means that it was not known by antiviral software.
Is it difficult? Not so much. There are already-made tools that are available for your disposal. You can find them on GitHub if you’d like.
Is it effective? Yes. Issue here is that such malware records everything and attackers needs to put some effort getting just what is interesting to them.
How to protect yourself and your users? Against 0-day? Patch, patch and once more patch in hope that it was previously reported or discovered by security researchers to software vendors, so it was silently fixed. Additionally, EDUCATE YOUR USERS. Knowing your way around the internet and most common attack vectors can decrease the probability of you or your Organization being compromised and fall prey to malware.
Local discovery
This is not the most effective method but works well on imagination. DuckDuckGo “red team physical security” and see what comes up. Or Google it. Whatever 😉
Is it difficult? Yes, you need to gain physical access to the office building or home to go dumpster diving, post-it notes hunting, etc.
Is it effective? Yes, once attackers have the password, they’re in.
How to protect yourself and your users? Always require MFA for all login attempts. But the users will hate you. And phone or physical key can be stolen, especially once attackers are inside the office.
If you see someone that wonders out of the ordinary in the office – ask what they are doing!
Password spray
This one’s easy. Attackers take a list of most common passwords, like this one (GitHub – iryndin/10K-Most-Popular-Passwords: This repo contains most popular and common passwords. To be used during user registration to prevent usage of common passwords) and run through the list against your username. This takes time but is, essentially, trivial. Attackers start the password spray script or use a tool and just sit and wait for the results.
If you’ve read the previous blog post (Passwords and why they suck | – Artur Rybarczyk –) you will know what is the issue here. Humans being humans set easy passwords that will be easily remembered. Password expiration policies can also lead to easier passwords that use a pattern and this gives us an effective password spray attack.
Is it difficult? Trivial. Not much to say.
Is it effective? To an extent. Millions of accounts are probed daily. Simple numbers game.
How to protect yourself and your users? Stop reusing passwords, start to monitor breaches, use password manager and, I can’t stress this enough, TURN ON MFA.
Brute force
Otherwise known as password cracking. I’m including it as this method is one of the most well known but using it during an attack is time consuming and requires getting encrypted passwords from your environment first. And this may not be so easily done.
Either way, after this first phase is completed, the cracking starts. Attackers will use software to try and guess the password, going through millions of passwords and combinations daily. It’s free and not so hard to use:
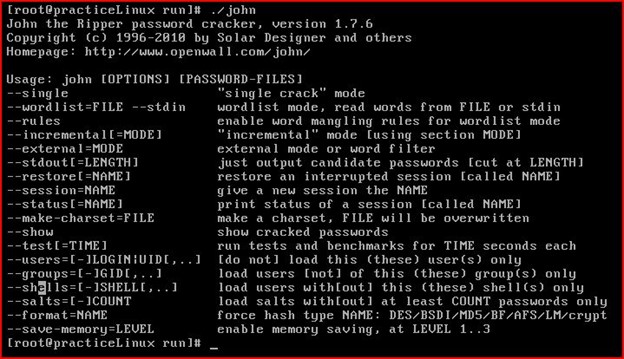
Source: John the Ripper Tool, XtraWeb
Is it difficult? Depends on the password. You can see sample stats below.
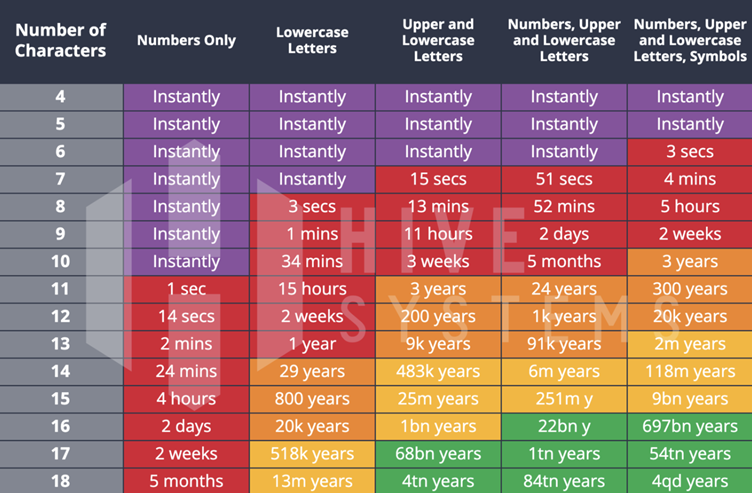
Source: Are Your Passwords in the Green? (hivesystems.io)
Is it effective? Up to a point. It’s a question of cost effectiveness.
How to protect yourself and your users? Have a complicated and long password. 20 characters should be enough. For now. And having MFA won’t hurt.
The solution?
I think you’ve noticed that MFA is a frequent reference of mine when it comes to protection against password attacks. And it is. As I’ve mentioned in previous post it will stop 99.9% of attacks against the accounts. You should have it turned on anywhere possible. But as you know, there are no perfect protections. MFA is no different and not all systems, apps or protocols support this solution.
Humans are still humans. We get lazy and grow complacent. People sometimes need to reset their MFA registration and admins are sometimes happy to do it over a simple phone call, which, and I again can’t stress this enough, is not a great idea. In a small company this may not be an issue, you all know each other and your voices, but when you don’t know everybody… how can you tell who is really on the other side of the line?
But that’s not all. As you may imagine if there is a new kind of security, there will be new attacks to exploit the flaws. MFA, once again, is no exception but you really must want to do that extra effort but that’s a story for another blog post.

